‘Cybersecurity Horror Stories’ was the theme of a recent webinar held by cybersecurity experts Huntress.
The assembled experts discussed a number of examples that could keep any MSP (Managed Service Provider) up at night!
Any unauthorised intrusion into a clients network can be a scary prospect.
Sometimes, it’s not always immediately obvious whether a login is legitimate, or something more insidious. Such as a threat actor who has phished credentials from a user through a deviously subtle sign-in form.
However, with the right approach to cybersecurity, MSPs and their clients can sleep a little easier at night.
Cybersecurity Horror Stories
The webinar was presented by three of Huntress’ expert security operations team.
Speakers:
- Chris Cochran, Chief Evangelist
- Dray Agha, Manager, Security Operations (UK)
- Herbie Zimmerman, Manager, Security Operations (US)

The team discussed a number of examples where accounts were suspected of being compromised.
According to the FBI, business email compromise (BEC), is one of the most financial damaging online crimes.
Huntress say their solutions are built for the SMB market (the 99%). With over 4,000 partners worldwide, and protect over 2.3 million endpoints.
For Huntress, their MDR (managed detection and response) for Microsoft 365 is a 24/7 service uses automation to monitor for suspicious behaviour across your network.
Potential threats are then verified by human SOC (Security Operations Centre) analysts to minimise false positives. Then a report is generated as a ticket, or emailed to the MSP partner, outlining the findings and recommending next steps.
Cybersecurity Horror Story Example #1 – Haunting in Eastern Europe
The first example, was about how it can be difficult to detect suspicious access without the visualisation that Huntress analysts get from the telemetry data supplied from the installed agents.
The example showed regular access from one user that always came from a geolocation based in Canada. In this case this account seemed to be logging in from the Ukraine instead, and it was enough to start a more manual investigation.
The visualisation supplies information like the IP address, geolocation and browser type, instead of a ‘wall of text’, enabling faster detection. The faster an anomaly can be detected and investigated, the less damage a threat actor can do in that time.
Without the visualisation, the anomaly could have easily gone undetected, and greater damage could have been inflicted by the threat actor.
When the report is sent to the partner, the anomaly is isolated, and the partner decides what to do next with some suggestions about what to do next.
Next steps can include:
- Rotating the user’s credentials
- Audit activity for the user
- Enable and enforce multi-factor authentication
- Enable complex conditional access policies for the user
If Huntress MDR detects a threat it automatically disables the account, but what happens next is up to the partner MSP.
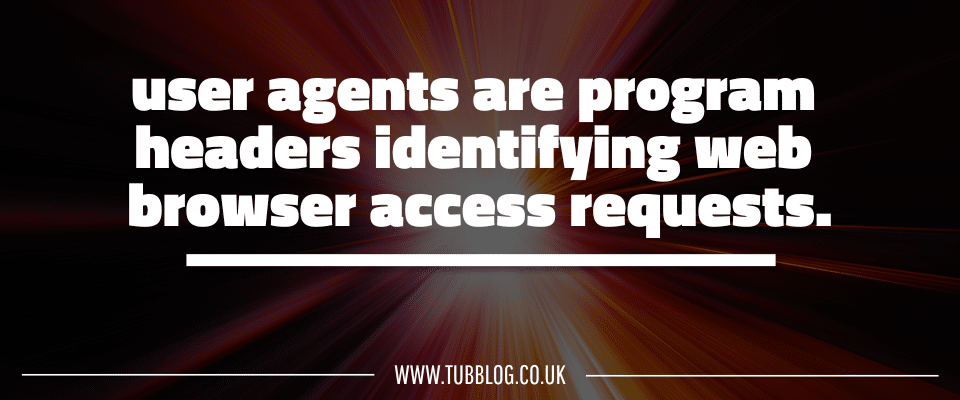
Cybersecurity Horror Story Example #2 – Huntress’ Totally Bogus User Agent Journey
The second horror story concerned user agents. User agents are like headers for programs that need to identify who is requesting access to a web browser.
It’s not as easy to detect anomalies with user agents, because of the range of devices any one user may be using.
A user may have a desktop computer at the office, as well as and laptop at home for remote working. They may also access their accounts through a tablet or smartphone.
Huntress’ automatic threat detection for user agents is minimal at the moment, and so that’s where the human analyst’s tradecraft comes in. With some manual investigation, some patterns were spotted in the logins, which the partner confirmed were not legitimate.
However, this sort of manual investigation isn’t a very scalable answer to this kind of problem. Yet, in flagging up these kinds of anomalies and applying the context, it can be developed into an automated solution further down the line.
There are two ways we can give context to this kind of threat in future, making them easier to spot.
- Firstly, we can assign this kind of threat a priority
- Secondly, we can develop documentation that bridges the gaps in our knowledge
Documentation needs to be easy to understand, but also flexible to keep up with an ever changing threat landscape. The purpose of documentation is to equip any analyst, no matter where they are based, with the information they need to be able to spot threats of this nature.
Cybersecurity Horror Story Example #3 – Spooky Subtleties
This horror story involved a threat actor creating an inbox rule, which moved emails from the inbox into the RSS feeds folder.
On the surface, this doesn’t appear too threatening. Users create inbox rules all the time where they forward emails to various places.
However, on closer inspection, although the user appeared to be working across two different geolocations, there was something different about the user agent in one of those locations. Hidden within the user agent was a telling piece of data – the IP address was not legitimate.
Sometimes, you need to dig a little deeper to find the anomalies and tells that give away a threat actor, and this was one of those cases.
Cybersecurity Horror Story Example #4 – Phantom User Agent
This user appeared anomalous due to the variance in login geolocations where their Microsoft 365 account had been accessed.
Again, Huntress’ visualisations were able to display all the geolocations the user had logged in from, for the analyst to see clearly. The problem sometimes with varied geolocations is that it could be down to the VPN the user may be using.
One of the ways you can tell if the logins belong to the same user is by the session ID, or the device name or the browser they’re using.
However in this case, the person had managed to hide the user agent data. It was done to cover their tracks, but in this case, the absence of any data at all made it even more suspicious. In addition to this, the browser type displayed as ‘Other’, making it difficult to identify which browser was used.
The huntress analysts isolated the account to prevent further ingress.
After receiving the report from Huntress, the partner confirmed that this wasn’t a false positive report. They then took action to disable the account and provide new credentials for the user.
It’s important that when something like this occurs, that action is taken swiftly, and that the information acted upon is correct.
The role of the security operations centre is take the appropriate initial action on the partner’s behalf, define the possible next steps and not report too many false positives.
Cybersecurity Horror Story Example #5 Nightmare on NameCheap Street
In the final example, the login record showed a user that started logging into their account in an unusual way. Again, the user agent was missing from the record, but this time they authenticated from a NameCheap domain.
NameCheap isn’t inherently disreputable, but it has been labelled as a ‘bulletproof host’.
Bulletproof hosts do not keep strict policies about what they host, and evade, or do very little about reports of illicit activity. Meaning they’re a perfect go-to for phishing websites.
The Huntress analysts hypothesised, that in this case, the threat actors employed a tool like EvilProxy to redirect the user to the NameCheap host server. It may have been the result of a phishing attempt.
What makes this a nightmare for the analyst, is that the information here is limited. They can’t tell if the user has clicked on something that they maybe should have. Therefore, further investigation and information from the partner is essential to make an accurate assessment.
It’s best to err on the side of caution in cases like this. You should flag it up as suspicious with all of the context detail you can provide.
Dray said: “User awareness is super critical in cases like this because only they will know for sure if the access was legitimate or not.”
The number one thing you can do for your SMB is to insist on regular user training to spot the latest scams and phishing techniques.
Having the best cybersecurity platform on the market is pointless, if the users you’re protecting have no security savvy.
Questions from the Audience
Q: Will Huntress be implementing an Incident Response solution?
A: Huntress are focusing on refining their SOC solution (EDR, MDR for M365 and Security Awareness Training) in order to keep partners and their clients safe as quickly as possible. Incident response requires a lot more investigation time, but there’s a big appetite for it to be developed in the future.
Q: Is it recommended that you install Huntress on a domain controller?
A: As there’s no need to do any event forwarding, you should install it on every asset in the environment. The more coverage Huntress has of your network, the better the picture the analysts have in spotting a potential threat.
Q: Microsoft alerts are typically slow to come through, would Huntress’ MDR for Microsoft 365 be faster?
A: Microsoft telemetry can be slow, so there is a delay in getting those critical alerts sometimes. Without bypassing Microsoft, Huntress’ analysts are able to employ a few shortcuts and respond faster, and with context.
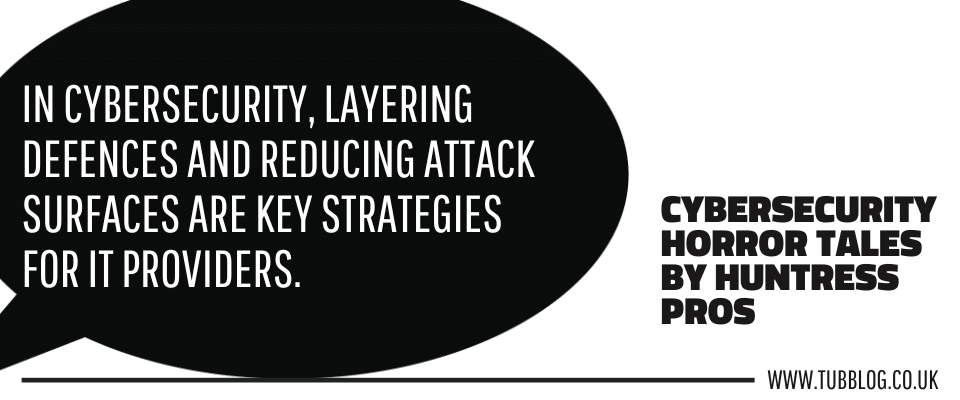
Depth of Defence in Cybersecurity
When it comes to cybersecurity defence strategies, both layering your security defences and limiting your attack surfaces are a good option for IT providers.
Chris gave the analogy of the tower defence games. In those games, you deploy an array of different defences to protect your base from attackers.
You cannot always prevent users from clicking on those realistic-looking phishing emails. However, with the right tools and the right training you can adequately protect your data.
With Microsoft 365, you can also impose stronger resilience through conditional access policies.
Conditional access defines what is permitted and the authentication required to access Microsoft 365. It can be used to limit access based on user/group membership, device type, geolocation IPs and much more.
Conclusion
This webinar was an interesting dive into the sorts of scenarios that Huntress MDR for Microsoft 365 may encounter. These examples can be difficult to read as threats at first glance, which is what makes them so alarming.
The more subtle the intrusion, the scarier the prospect that a threat actor could be causing more damage the longer they remain undetected.
Huntress try to manage the balance between accuracy in their reports and a speedy response. However some of the scenarios displayed in this webinar have proved that it’s not always easy to get right.
Have you experienced a spooky encounter with a threat actor accessing your client’s data? Have you let your guard down because of alert fatigue in the past, and it’s been a costly experience?
If you would like to share, we would love to hear your story in the comments.















Comments