As we know, the cyber threat landscape has seen the frequency of attacks increase at an alarming rate over the past few years. Cybercrime has become big business, and technological advancements have seen the popularity of smart devices soar.
However, the fast adoption of these smart technologies brings with it some risks, as well as opportunities.
In this article, we take a look at the types of threat that affect Internet of Things (IoT) devices, and what you can do to mitigate the risks.
The Rise of the Internet of Things
Greater wireless connectivity opened the door for a number of small innovations designed to make our world easier and more convenient.
Thanks to low-cost computing, the cloud and mobile technology, physical devices can collect and share data with minimal human interaction. Independent, connected devices can record, monitor and adjust their settings according to set parameters or based on other data. They’re sometimes called smart devices.
Some examples of common, everyday smart devices include:
- Voice assistants
- Baby monitors
- Thermostats
- Video doorbells
- Smart speakers
There are many ways that smart technology interacts with the environment it inhabits. For example, smart speakers react to voice commands. Whereas an air pollution monitor may react to toxins in the air. A smart thermostat may control the temperature of the rooms in your home, and a video doorbell can record movement according to defined parameters.
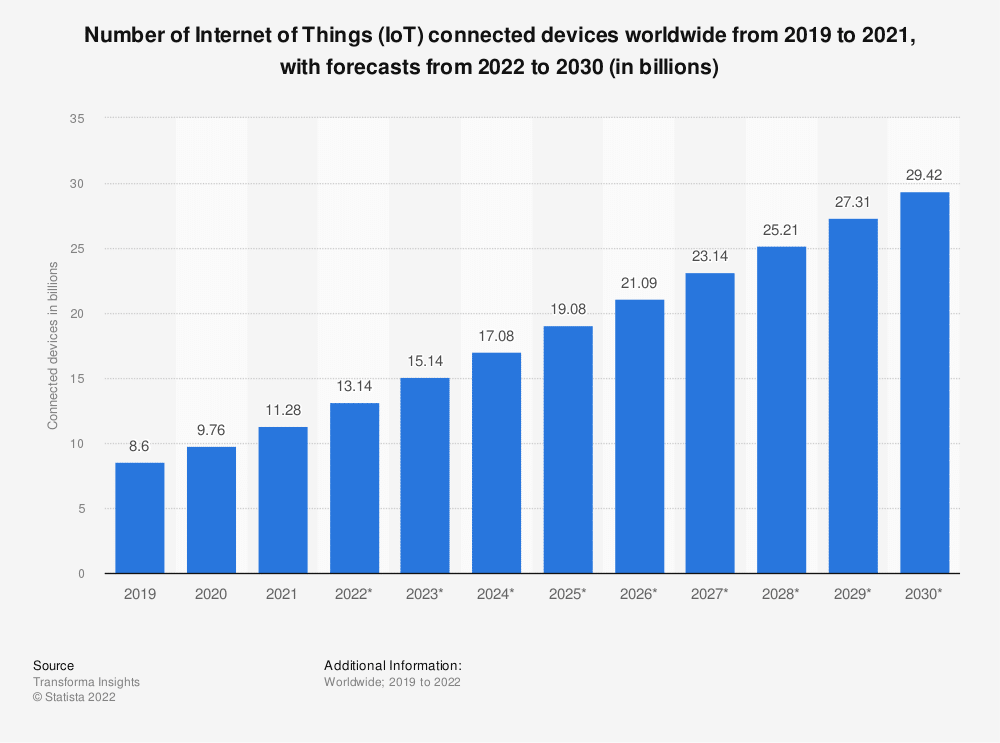
According to Statista, the market for smart tech in U.S. households is growing by approximately 12% per year. Since 2019, the number of worldwide connected devices has nearly doubled, and looks set to double again by 2030.
There are also industrial applications for IoT too, including technology involved in logistics and supply chains, manufacturing maintenance and safety.
Emerging Trends in Internet of Things
There have been some great technological leaps forward through the use of the IoT, and more still to come in the future.
Here are four trends that IoT has helped progress forward:
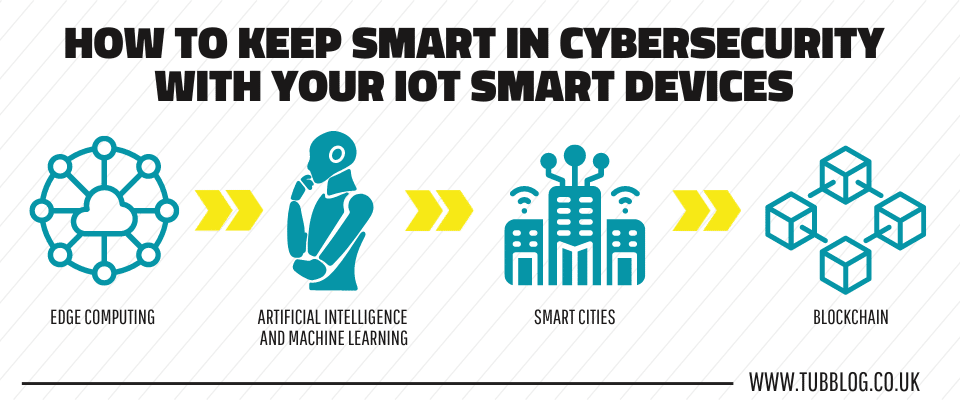
Edge Computing – this involves data processing on the device itself, rather than just collecting and sending it to the cloud. The advantage of edge computing is that it helps to reduce latency and enhances security. This means it’s generally more secure and can process data on the device and not through the cloud.
Artificial Intelligence and Machine Learning – The data collected by IoT devices requires a level of automation to function without the need for human interaction. This is where AI and machine learning can elevate IoT functionality beyond simple programming. With many IoT devices working in tandem, the possibilities for automation continue to be developed.
Smart Cities – these are modern urban connected spaces that use smart technology to provide a number of benefits. They help councils and governments manage traffic, utilities, waste management and other community services.
Blockchain – Blockchain, sometimes referred to as a Distributed Ledger Technology (DLT), is a peer-to-peer record of assets and transactions. It is a decentralised system where a transaction, once recorded, cannot be undone or tampered with.
Advantages and Disadvantages of IoT in Business
For businesses, there are a number of advantages that can be gained from utilising smart technology. However, there are some limitations as well, which you should be aware of before investing in IoT.
Advantages of IoT
Due to the large amount of investment in I0T, smart devices are affordable and easy to scale. They allow for increased productivity, safety and flexibility, and sensory devices can retrieve a lot of real-time data that can allow for quick automated responses.
IoT can help with:
- Reducing operational costs
- Improving work safety
- Improved customer experience
- Increased efficiencies in supply chain
- More business opportunities
Disadvantages of IoT
As IoT is still a relatively new technology, there is not yet a standardised approach for compatibility. Also, some complex IoT infrastructures can be difficult to manage if changes are required. With a large network of interdependent devices, it can take a high degree of expertise to get the best out of the technology.
Some of the areas for concern are:
- Security and privacy concerns
- Reliance of connectivity
- Lack of international standardisation
- Complex infrastructure
- High skill requirements
An IoT deployment project can be a difficult undertaking if you’re not prepared for the amount of project work involved. In addition, there are can be complex ongoing support requirements too. However, the benefits are many.
As always, you as the trusted IT partner need to make your client aware of both sides if they decide they want an IoT solution for their business.
A New Vector for Cyber Criminals
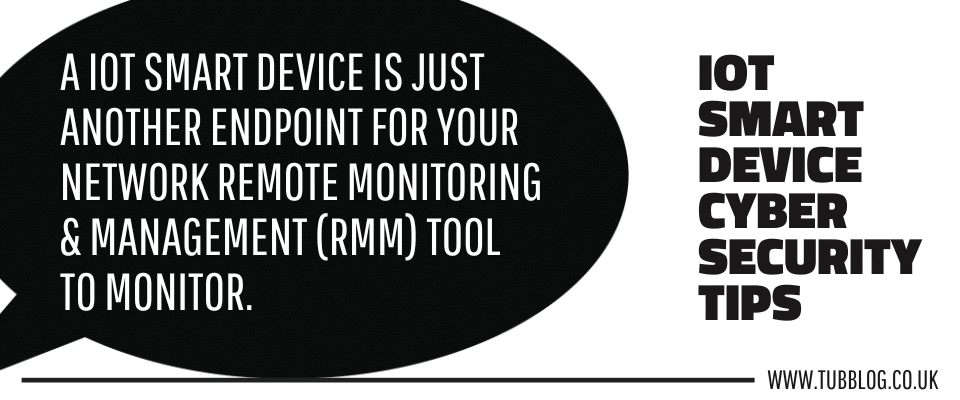
An IoT smart device is just another endpoint for your network Remote Monitoring & Management (RMM) tool to monitor.
There is a tendency for smart devices to not have as much built-in security, and so there is definitely a need to think about ways of making them safer and less exposed.
Like any endpoint, there is a risk of malware infections if not properly protected.
A connected device, which is broadcasting data, can be easily disrupted with a Distributed Denial-of-Service (DDoS) attack. Whereas any device that utilises a camera or a microphone can be used for espionage – to spy on your customers to gain an advantage.
Shadow IoT
Depending on how the device connects to other devices, there could be a number of ways your smart device may be at risk. Poorly protected Wi-Fi routers may be a perfect backdoor for cyber criminals. Bring Your Own Device (BYOD) has become a popular model for businesses since the pandemic for laptops and smartphones, but this can also apply to IoT devices too.
It’s not just Wi-Fi that’s at risk. The BlueBorne exploit is an example where an unpatched Bluetooth connection can be an easy attack vector for hackers. It’s anticipated that the rollout of 5G may also see development of similar exploits as well.
Software/Hardware Vulnerabilities of IoT
Another area for concern is out-of-date software or firmware on a device. Keeping on top of this requires managing it in your professional services automation (PSA) tool. Failure to do so means leaving your devices open to exploitation.
The other thing to be aware of is the vulnerability of the physical layer of an IoT device. If attackers can access the device directly, they can copy any data, or change the devices programming, which could be very costly for your business.
A Few Illustrative Examples of IoT Cyber Attacks
It might not be immediately obvious how damaging a cyber attack on smart devices can be, so here are some examples to illustrate their effects.
The Mirai Botnet
The Mirai Botnet was an attack that happened in October 2016. The botnet spammed a DDoS attack against, amongst others, Dyn, an internet performance management services provider.
It did this by spreading a virus that would search the internet for IoT devices that used well-known default usernames and passwords.
It resulted in taking down a number of major websites and services, including: Twitter, Netflix and CNN.
The Verkada Breach
Verkada, a cloud-based video surveillance service, was hacked in March 2021. It was done as a demonstration to show how prevalent surveillance is.
The hackers gained access to 150,000 video feeds, in hospitals, prisons, banks and mental health institutions. Big corporations, including Tesla and Cloudfare, were also compromised.
It turned out that roughly 100 Verkada employees had ‘super admin’ privileges, which was how the hackers easily accessed the feeds.
The Stuxnet Worm
Probably one of the most infamous attacks on IoT was discovered in 2010, at a uranium enrichment plant in Natanz, Iran, although the first breach happened almost a year before. The Stuxnet Worm gained access to the centrifuge program logic controllers, allowing the worm’s developers to access privileged information about the uranium gas enrichment process, as well as sabotage it.
It’s believed that the attack led to 984 uranium centrifuges being damaged by the attacks, leading to a 30% reduction in uranium enrichment efficiency.
How to Mitigate IoT Security Risks
There’s a proverb in IT security that holds well here: “If you connect it, protect it.”
An unprotected network can allow hackers to take control of devices using malware. Once they have control, they can turn sensors on or off, spoof data, spam the network or use cameras for the purposes of spying.
Though not an exhaustive list, here are eight general rules of thumb for IoT security to help you mitigate the risks:
- Secure Your Connection – The network should be private, encrypted and firewalled. A virtual private network (VPN) is best.
- Enable Two-Factor Authentication – Applications used by IoT devices should have 2FA where possible.
- Use a Secondary or Tertiary Network – Do not limit all of your IoT data to a single network stream.
- Buy Quality IoT Products – look for higher-end products with better built-in security over cheaper similar devices.
- Get Certified – and consult whatever framework you’re using for the latest updates.
- Keep on Top of IoT Security Updates – be aware of how regularly you need to check for updates with the manufacturer.
- Keep controlled access to privileged admin accounts to a minimum.
- Do not leave devices in their default setup or pairing mode. This makes them vulnerable to physical layer manipulation by third parties.
IoT Security Awareness Training
We must never forget the importance of the human factor when it comes to cybersecurity. This applies to the Internet of Things too. In the past, it was all to easy to believe in the ‘set it and forget it’ practice of deploying new kit.
You should think about the end-users who will be responsible for the data capture. How regularly will they will need to be given cybersecurity awareness training?

Regulation and Compliance for IoT
In the UK, the Product Security and Communications Infrastructure Act 2022 will come into effect in April 2024 in an effort to make smart devices more secure.
The standard covers three main areas for smart device manufacturers to comply to:
- Consumer IoT devices will not be allowed to have universal default passwords
- Consumer IoT devices will have to have a vulnerability disclosure policy
- Consumer IoT devices will need to disclose how long they will receive software updates
Prior to this act, the Code of Practice for Consumer IoT Security was published by the UK Government in 2018 as a set of voluntary guidelines.
A similar framework exists in the US for the National Institute of Standards and Technology (NIST) to set out guidelines for federal agencies using IoT devices.
The groundwork for this act comes from European Standards Organisation (ESO) ETSI, who released the first globally accepted standard for consumer IoT security: ETSI EN 303 645
The regulations are there to set a framework for manufacturers, but there is still a role to play for IT service providers who include IoT in their offerings. They will have to ensure that any devices procured from April 2024 meet the compliance rules set out above.
The Internet of Things In Summary
The potential for smart technology for small business enterprises (SMEs) is huge, but it can be risky, and expensive if you get it wrong.
The important thing to remember is that you should treat smart devices as you would any other endpoint in terms of cybersecurity.
Additionally, regular software updates on devices is encouraged for best practice. Pay for quality from reputable manufacturers. If a manufacturer is not producing regular updates, for example if the product line is not longer being supported, then consider replacing with a more recent model.
As the rate of adoption for smart devices continues to soar, so will the inevitable draw to cybercriminal syndicates. The idea of IoT is to make things easier for businesses, but this can only happen if these devices remain safe and secure.
Future legislation will apply some basic protection, but there will still be a need to do due diligence, as with any technology.
Are you responsible for the security and maintenance of smart devices in your MSP business? Have you been thinking about deploying IoT technology but have your reservations?
We’d love to hear about it in the comments.












Comments