One of the ways cybersecurity experts Huntress continue to innovate and meet the needs of their customers is by holding regular webinars like the Product Lab.
Both educational and interactive, these online presentations encourage engagement from their community audiences in how to better align their managed security platform. And they’re a great way for partners to see how the product is developing to address growing security threat landscape.
Attending September 2023’s Product Lab, we saw some of Huntress’ recent developments as well as a couple of deep-dives into session/cookie hijacking.
The Product Lab
The two main speakers were:
Kyle Hanslovan, CEO of Huntress
Chris Bisnett, CTO of Huntress
with a guest presentation from:
John Hammond, Principal Security Researcher for Huntress
The hour-long webinar set out to provide updates, and to educate partners on some of the current developments, as well as the important security trends that we all need to be aware of.
Straight Outta the Lab
To kick off the Product Lab agenda, Kyle went through some of the new developments from the Huntress team. Here are a few examples:
1. Halo PSA Integration Beta
A new integration for Halo’s professional services automation has been added to the Incident Reporting section of the Huntress platform.
2. Call and Text Notifications
You can now opt-in for text and call notifications to be sent to key contacts in an attempt to accelerate outreach during critical incidents.
Currently available in the US and Canada only at the moment, but should be rolled out internationally in the future.
3. New HIPAA Episode Released
A new animated security training video has been released on the subject of Health Insurance Portability and Accountability Act (HIPAA). The protection of patients’ health data is similar to that of GDPR in the UK, and requires the custodians of such information to meet a particular standard.
4. Awareness Training Pipeline
Some updates listed as headlines, which included:
- Huntress SOC Curates Your Training Plan
- Improved TOTP/Authenticator Support
- Knee-Deep Managed Phishing
- Building Co-branded Reports for End Users

If not Logins, Then What?
Chris took over lead of the presentation to talk about the differences between events and sessions in Microsoft365.
M365 events show the actions a user makes. An event log can tell you who’s logged in, when permissions are changed and what is accessed. However not all events are logged.
M365 sessions are unique IDs that connect the events that occurred during a particular session. This is useful because it can reveal activity across multiple devices and can be used to see how a potential threat actor has altered items across your system.
Challenges
There are some issues or challenges that make identifying events and where they’ve occurred difficult to track and stop.
- Without establishing conditional access rules, sessions can last forever.
- Not all events have a session ID attached. This could be because the event has been generated by an application, or if multiple events are created at the same time, it may only attach the session ID to the first one created.
Hijacking Sessions, Why Do It?
A threat actor will look to hijack a session because logins are already authenticated and multi-factor authentication confirmed.
A hijacked session doesn’t look suspicious at first glance because it’s not a session ID. Traditional SIEM (Security Incident Event Management) software finds it difficult to identify and isolate. Furthermore, phishing is a good way to steal a session.
Stealing Browser Cookies
Browser cookies are how a website identifies you and your preferences on it, which includes web-based email. They pre-verify you, and so are of value to hackers. Malicious browser plugins are an ideal way to steal your cookie data, as well as malware on open, shared devices.
Cookies are a way to make it easier for you to access what you need to without being continually asked for your credentials. Cookie data is something that is bought and sold on Darkweb marketplaces, such as the Genesis Market.
![]()
Product Lab Hacker Demonstrations
John Hammond took over the presentation to show us a couple of demonstrations from the point of view of the victim and the threat actor.
First Demonstration
The first demonstration was a basic look at how easy it is for a threat actor to gain access to a victim’s email, using a session cookie obtained via the darkweb.
It demonstrated how browser cookies can bypass logins and passwords, allowing the cookie-bearer to assume the identity of the user and access their private spaces on the internet.
Second Demonstration
The second demonstration was a little bit more sophisticated and had the threat actor obtain a session token by first phishing the victim with a simple Microsoft-branded email giving them a link and a ‘secure code’ to enter.
The link returned a prompt for the user to input their login and password details.
Then, using a PowerShell script called Token Tactics, there were able to obtain all the session token details to access whatever they want to.
With just a few clicks, the threat actor could replace authentication fields with the stolen session token data.
Although I didn’t fully comprehend how the attack worked, it was clear that it was something that was quick and easy for professional hackers to do.
Detecting the Hacks
Due to the nature of session and browser hijacks, they can be quite difficult to detect. Therefore, multiple methods need to be employed to detect them.
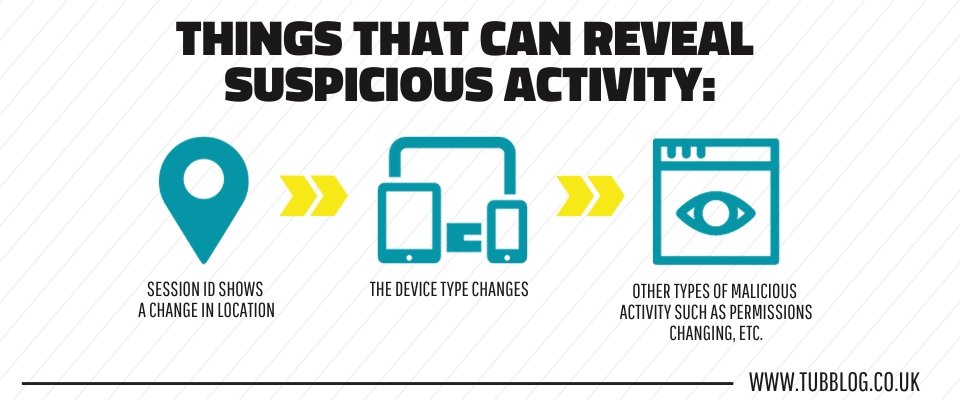
Things that can reveal suspicious activity:
- Session ID shows a change in location
- The device type changes
- Other types of malicious activity such as permissions changing, etc.
Audience Q+A
To round off the Product Lab agenda, some time was set aside to give the community a chance to field questions to the speakers.
Here are a few examples of the questions that were asked, along with the answers the panel gave:
Q. Would conditional access prevent or mitigate the problem of session hijacking in Microsoft 365?
A. Conditional access requires a successful login first, so it wouldn’t prevent a hijack attempt on the first login.
Q. How can we capture endpoint logs for compliance and insurance purposes?
A. It’s not something available at the moment, but it’s in the development pipeline for the future.
Q. Is there a way to turn off email notification for unresponsive agents?
A. Yes, this is something you can turn off and on yourself.
Conclusion
A monthly, interactive webinar such as the Product Lab is a great way to deliver value to your partners. By educating them about security trends, informing them of product updates and listening to what they want to see developed further, Huntress are demonstrating an investment in working to make their partners’ businesses more secure.
I’d highly recommend that MSPs interested in cyber security sign up to attend the monthly Huntress Product Lab sessions.
This is definitely the way forward for vendors, particularly those that are security-conscious, where technology needs to remain at the cutting edge.
Taking on board the input from partners and proving you’re listening to them shows great commitment.
What do you think of these kinds of product improvement webinars? Do they provide value and are they worth your time?
We’d love to hear about it in the comments!
And if you’d like to know more about the Breaches and Brews, the informal get-together roadtrip to introduce UK MSPs to Huntress, read our blog here.











Comments