The cyber attack stories we hear as Managed Service Providers (MSPs) are often the ones we’re a little bit embarrassed about mentioning. Because our IT defences, or those of our peers, are compromised.
As MSPs, we are constantly being told by software vendors all about the best practices for providing great cybersecurity for their clients. However, not all MSPs put this advice into practice as effectively as others.
What do we do when something slips past the defences? And what about new customers who come to you after they’ve already suffered a cyber attack?
CompTIA’s UK and Ireland Community staged a really informative event on cybersecurity, giving a full 360 degree perspective of a cyber attack.
This article captures some of the highlights.
Untold Cyber Attack Stories: An Introduction
The event took place at Millennium Point in Birmingham, UK, on Thursday the 18th January 2024. Although the meeting took place across an afternoon, there was much to cover in the time.
The meeting started with welcome introductions from the UK & Ireland Community Director, Leanne Johnson.
Then, Zeshan Sattar, CompTIA’s Senior Director of Learning and Skills Certification, gave an overview of their Cyber Ready Programme. It’s a six-month free programme aimed at getting returnees and the unemployed trained, certified and into cyber careers.
The programme is looking for candidates from Lancashire, West Yorkshire and the West Midlands.
With a particular focus on hard-to-reach groups, such as:
- Women
- Ethnic minorities
- Neurodiverse
- Those affected by poverty
Cyber Attack Stories: Threat Landscape Update: Where Are We Now?
Datto‘s Greg Jones stated why cybersecurity was important to all of us, and why it’s integral to all businesses and their success.
We are living in a golden age of tech. It’s a great time to be an MSP with £50bn being spent worldwide on the cybersecurity market.
However, attacks on the rise, and here are some of shocking statistics Greg shared:
- 300% increase in reported cyber crimes since the Covid pandemic
- 92.7% ransomware attacks have nearly doubled
- 59% of MSPs said remote work increased ransomware attacks
Cyber Attack Stories Threat Landscape Highlights
Some of today’s cyber threats include:
- Hybrid Environments – 74% of SMB/SMEs are still operating a hybrid environment – a huge opportunity for bad actors
- Unsecured Public Networks – Secure business data is being transmitted across public and home networks
- Smaller Businesses Targeted – Ransomware is targeting SMBs and MSPs more and more, moving away from large enterprises
- Cybercrime on the Rise – It overtook real-life crime a few years ago
- AI, Generative AI and Machine Learning – They have enabled bad actors to accelerate their attacks
- Login Credentials Bought and Sold – Either on the black market, or blue collar workers asked to install a device for cryptocurrency
- Unpatched IoT Devices – Exploits through unpatched or unchanged passwords on smart devices are on the rise
Threats are coming from a variety of different sources too.
Not just organised crime collectives and nation state attackers, but hacktivists, insider threats, and developer syndicates are all looking to capitalise on exploits in your systems and software.
Time allocated in your business to conduct a security audit is time well spent, so don’t leave it.
Set a date to conduct one today!
Untold Cyber Attack Stories: The BIG Customer Hack
Andrew Allen of Aabyss shared with delegates a personal story about a business that approached his MSP following a devastating cyber attack.
He started his story by saying that while the MSPs in the room were pretty good at what they do, there are many others out there that aren’t as good.
A credit union, who wasn’t a client at the time, called into Andrew’s helpdesk looking for help. They were desperate and looking for someone who could assist them in the wake of a cyber attack.
The credit union’s previous IT company had abandoned them, and data had been missing for months. They were hoping that Aabyss could provide a magic panacea to sort it all out.
After some investigation, it turned out that their previous IT provider had left a port open on their firewall, which gave the cyber attackers easy egress into the credit union’s data.
They ransomed the data, demanding a huge fee. The police advised them to just pay it, off the record.
Fortunately the CEO of the credit union had managed to keep paper records of transactions, but it still took a couple of weeks to roughly put things right. It was a lot of stress for the staff, but the community came together to support them.
Andrew was happy to say that despite harsh penalties from the Financial Conduct Authority from the gross negligence of losing customer data, the credit union is still going today, and still a customer of Aabyss.

Understanding the Why and What Behind an Attack
Lewis Warner of Pentiq gave a presentation explaining the terminology associated with cyber attacks and the ways to reduce the risks against these attacks.
Risk = Asset+Vulnerability+Threat
For example:
- An asset could be customer data
- A vulnerability could be an unpatched zero-day software exploit
- A threat could be malware
Cyber Threat Actors (CTAs) are participants or groups engaging in hostile or malicious actions using computerised systems, devices or networks.
Some CTAs include:
- Cyber Criminals
- Hacktivists
- Nation State
- Terrorists
- Insider Threats
Thinking Like an Attacker
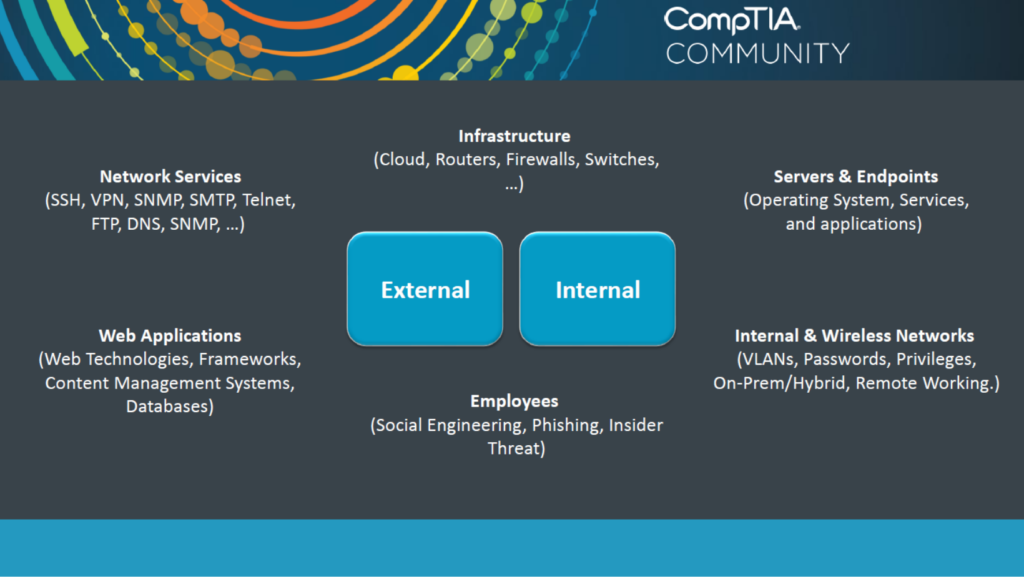
Lewis said that to think like an attacker, you’ll need to be aware of the places you can find information to make your hacking attempts easier.
Data that make hacks easier can be found all over the internet.
On the surface web (company website and social media), you can find out contact information, job vacancies, deployed technologies, etc.
The deep web holds more sensitive information, usually safeguarded, such as legal documents, medical records and academic information.
The dark web is where you find illegally brokered information on the black market, or sensitive financial data.
Compromised passwords are a common way for attackers to gain access to your data. Passwords can be cracked a number of ways:
- Brute force
- Key logging
- Data breaches
- Shoulder surfing
- Stealing passwords
Never use the same password across multiple systems, and always change the default administrator password.
Misconfigured or unpatched servers are another way for attackers to gain easy egress. Ensure you have automated patch management in place to prevent those known exploits being used by attackers.
More Good Practice Tips
- Keep configuration up-to-date
- Have user access controls in place
- Practice good password hygiene
- And attend events like this one for greater awareness!
Untold Cyber Attack Stories: The BIG MSP Hack
Greg Jones talked to Ken Roulston of EX2 Consultancy about a particularly nasty cyber attack his company suffered following an acquisition of another MSP.
Ken paid the ransom of £0.5m, but the total cost came to about £1m in the end, due to lost business.
Ken has over 40 years of experience in the IT industry, and he started his MSP in 2009. He grew his business through the acquisition of smaller MSPs.
Picking a Rotten Apple
In 2021, after integrating an acquired business, he suffered a hack three days after announcing the takeover publicly. It appeared that the hackers had done their research over a number of months and chose their moment to strike.
They had made a copy of their data and threatened to sell it on the dark web if the ransom wasn’t paid.
After a little investigation, Ken realised that the data was gone, and the backups were missing too. Not only had the data been stolen, but the compromised system’s data structures had been trashed too.
After paying the ransom, it took Ken’s team a full two weeks to rebuild the systems working day and night.
Though the acquired MSP hadn’t done anything wrong, per se, their security practices could have been much more robust. A combination of lacklustre security practices and human error were found to be the root causes of the hack.
Untold Cyber Attack Stories: MSP Q&A
Q: How did your staff react to what was going on at the time?
The stress affected the engineers almost to the point of PTSD. Ken brought it external counsellors to help them to cope with the excessive workload.
In the end, it was one of the factors that contributed to Ken’s decision to sell his business.
Q: How did you communicate with the hackers?
Ken’s Technical Director did most of the communicating via the dark web. They operated 24/7 in shifts and gave out a helpline chat for any questions.
When they consulted with a government advisor after being hacked, the advisor told them that this group were one of the more reputable ones. As in, if you were to pay them, they would actually give the data they took back.
Just like a major corporation, their reputation matters to them. Ken remarked, it was laughable, given what they’re doing for a living.
Q: Did you have cyber insurance?
The acquired company didn’t have any cyber insurance in place because the CEO didn’t trust any providers to try and get out of paying a claim.
Q: Was it the worst two weeks of your life? How did it affect you?
Ken said he took the incident far too personally, and the stress of it affected his marriage and his mental health.
Q: How has it helped the business?
The business invested much more in technology to reduce the likelihood of an attack, and developed a more robust response plan.
Cyber Attack Stories: Lessons Learned
He advised us in the room to practice what we preach and ‘eat our own dog food’ when it comes to cybersecurity.
During the acquisition, Ken did due diligence on all aspects of the handover process, with the exception of the technical details, which he took on faith. However, he’s learned why you should not take shortcuts when it comes to the technical side. It was an expensive, but important lesson.
Now Ken is giving back to the industry by sharing his awful experience. Hoping that by doing so, he might help others.
Cybersecurity Focus on the West Midlands
Holly Whittles from Purple Frog Systems gave a presentation on cyber crime in the West Midlands, and the resources that are being spent to make digital safety for businesses more robust.
Some of the highlights mentioned included:
The Cyber Quarter – a security collaborative hub based in Hereford
The West Midlands Cyber Resilience Centre – a resource dedicated to protecting businesses in the West Midlands
The West Midlands Five-Year Digital Roadmap, dedicated to:
- Securing access to digital opportunities for all, especially those in poverty
- Sharing and using data to improve people’s lives
- Becoming the UK’s best connected region
- Realising the potential of digital to transform the local economy and build economic resilience
- Using digital public services to build a fairer, greener and healthier region
What Happens in the Event of a Cyber Attack from an Insurance Perspective
Clear Insurance Group’s Trevor Cornbill delivered a walkthrough of what you should do in the event of a cyber attack so as not to invalidate your claim.
To avoid the chances of your claim being denied, Trevor advised that you:
- Conduct regular reviews to make sure you have the right amount of cover
- Provide a detailed and accurate description of your business
- Make sure you have a clear understanding of the questions and what’s expected of you
What Happens in the Event of a Claim
Trevor explained the five steps that occur from when a ransom demand is received.
Stage 1: Notification
As soon as you receive notification of a hack or a ransom, you need to call your insurer immediately. That is so that a case can be raised and a team assigned to work with you in the background.
Stage 2: Assessment
What needs to be done. Legal requirements and public relations. Notify your customers. This service can be done by your insurers.
Stage 3: Forensics
A deep dive to see how the bad actors got access. What was taken or compromised, and what can be done to prevent it in future.
Stage 4: Recovery
Getting your business back on its feet again. Restoring backup data, and putting measures in place to make your environments more secure.
Stage 5: Settlement
Loss of income/revenue can be covered by your policy in the final settlement.
Trevor said that all MSPs should encourage their clients to take out a cyber insurance policy.

What You Need in Place from a PR Perspective
Another thing to do when you are the victim of a cyber attack is manage public relations. Rahme Memet from TechComms gave us an overview of crisis management, and why we should have a plan ready for when the worst happens.
She described a PR crisis as any kind of negative public attention.
This can be:
- Technological
- Personal
- Financial
- Organisational
- Natural Disaster
Reputational damage is so much more common thanks to newsjacking on social media.
An good example of this was the Gender Pay Gap Bot that did the rounds on Twitter.
If any Twitter account tweeted with the hashtag: “@IWD2023”, the @PayGapApp would retweet the tweet with the company’s gender pay gap information according to government data.
Another significant PR disaster occurred when the Silicon Valley Bank released a statement about recent losses in March 2023.
To their customers, it looked like they were in a financial freefall. Even though, at the time, the bank was still cash positive at the time.
As a result, following the statement release, customers quickly withdrew their money and the bank collapsed in 36 hours.
Having an Effective Crisis Management Plan
A good crisis management plan covers two aspects:
- Respond and manage the incident
- Communicate with your clients
When responding to a crisis caused by a cybersecurity incident, you should:
- Establish the FACTS
- Develop a CLEAR communication plan
- Communicate IMMEDIATELY and effectively
- MONITOR and evaluate the effectiveness of your communications
You PR Crisis Management Plan should anticipate the questions your customers and shareholders are going to ask.
And remember that whatever answers you give, must be truthful. Else you risk even further reputational damage further down the line.
Untold Cyber Attack Stories: Resources and Event Takeaways
CompTIA’s Wayne Selk gave us an overview of some of the ways CompTIA’s cybersecurity programmes can help.
All businesses are focused on risk, and the key to growth and increasing our revenue is reducing that risk. He talked about the supply chain, skills gap and legislation, and how CompTIA can help solution providers.
Then, Kyle Torres of Sophos rounded off the event with a recap of the key takeaways.
He raised an interesting point about whether or not we should be accepting clients without adequate cyber insurance, and how we should be educating clients on risk, rather than selling them on what areaas of their business our cybersecurity product can protect.
He proposed that perhaps we should be looking to offboard clients who aren’t prepared to take cyber security seriously.

Untold Cyber Attack Stories: Event Conclusion
It’s easy to sell clients on how well your products can protect their data and systems. However, it’s not always easy to tell them what they should have in place for when those defences fail.
Yet, those failovers are exactly what every business needs in place for when the inevitable happens. How resilient, or how quickly can your business get back on its feet after an attack?
What cost are you prepared to pay? How capable is your PR machine in limiting the damage to your reputation, and is your insurance cover appropriate for your needs?
This was a great example of why the CompTIA Community are so good at holding events that open up the dialogue on why cybersecurity is so important. To hear frank accounts of when things go bad, and what to do in the terrifying circumstances of suffering a breach.















Comments