In the world of cybersecurity, threats are constantly evolving.
Therefore, by throwing a spotlight on 2024 cyber trends, we can adapt our defences and anticipate new emerging threats.
Artificial intelligence will play a very important part in both threat delivery and threat detection and prevention.
Two recent webinars from Barracuda MSP look at the recent trends in cyber. And they look deeper into how AI is empowering the type of threats we’re seeing that are affecting email.
Spotlight on 2024 Cyber Trends
The first of the two webinars focused on which of the trends we saw in 2023 to watch out for in 2024. This involved looking at the key observations from the Security Operations Centre (SOC) and the key incident statistics.
Presenters:
Sr SOC Manager, Defensive Security Barracuda MSP
and
Cybersecurity Analysts Manager, Barracuda MSP
Key Observations from the SOC in 2023
The six main observations were:
- Ransomware at an all-time high
- Ransomware-as-a-Service (RaaS) increases the scope of targets
- Threat actors are becoming much more persistent
- Attack lifecycles are extended
- Threat actors are more effective
- Successful attacks having higher impact
It means that the overall sophistication of attacks has improved, and had a bigger impact throughout 2023.
2023 Incident Statistics
- Ransomware attack frequency up 95% since 2022
- $265 billion estimated total losses from Ransomware in 2023
- 4000+ organisations’ data published on dark web
- Average ransom amount: $100k/$5 million for smaller/larger organisations
- Average recovery time: 3 weeks per incident
All of this doing a significant amount of damage financially and reputationally.
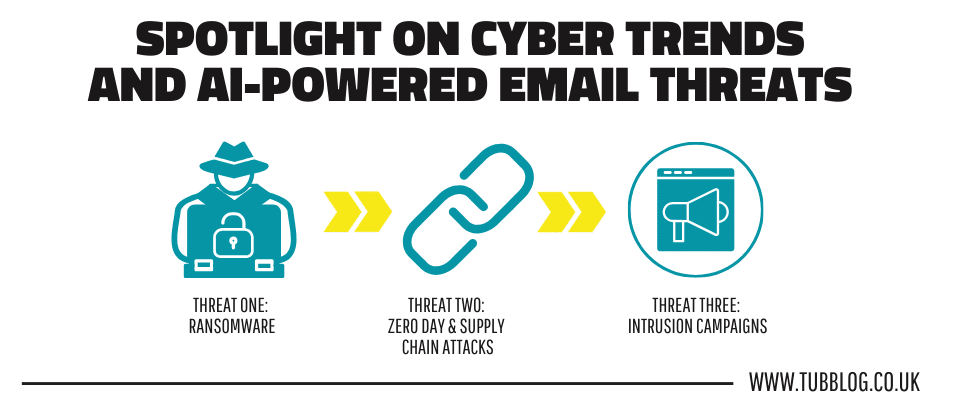
The Top Three Threats of 2023 According to the SOC
Threat One: Ransomware
Ransomware groups are outpacing endpoint protection utilities, with driven by increased demand for RaaS in the dark web.
Attacks are executed using legitimately licenced tools, (such as RMM, remote desktop and VPN).
Ransomware attacks are detrimental to any business. Data is exfiltrated and exposed, and networks are paralyzed. While the costs, both in time and money, to recover are immense.
Advanced endpoint protection managed by a dedicated, security-first team is the best way to mitigate this problem. Maintain regular segregated backups, and ensure cyber insurance cover is up-to-date.
Threat Two: Zero Day and Supply Chain Attacks
The threat of Zero Day attacks have exponentially increased, partly due to more applications in service across the supply chain, meaning greater exposure.
The impact of this is that threat actors have the ability to quickly compromise organisations’ networks at scale, even when other security controls are in place.
This can be mitigated through effective patch management and emergency patching plan for contingencies, with clearly defined roles and responsibilities.
Threat Three: Intrusion Campaigns
Attack surfaces are increasing all the time through gaps such as misconfigured cloud security controls.
Threat actors can quickly move laterally, elevating privileges to establish command and control.
You can be better prepared by conducting external scanning and penetration testing. Always implement MFA, and practice better privilege management. Improve network segregation and regularly review firewall and network access policies.
Takeaways from 2023 Cyber Landscape
Advanced Persistent Actors (APT) are adapting and advancing in sophistication, and growing in numbers.
The volume of attacks an organisation faces on a regular basis is increasing exponentially and security teams are struggling to keep up.
Consumer data exposure is a huge risk, and personally identifiable information (PII) is a pot of gold to threat actors.
A Look Ahead to the 2024 Cyber Trends
Malicious actors will be using artificial intelligence to drive more complex attacks. Utilising malware-friendly large language models (LLMs) like WormGPT and FraudGPT, and providing AI-as-a-Service to other threat actors. Enabling them to attack at scale and without requiring advanced skills in-house.
Some of the types of attacks we’ll see will involve:
- AI-Powered malware
- Generative AI phishing campaigns
AI-Powered Malware
AI-powered malware is malware code written by an LLM, for example BlackMamba.
The benefits of AI-powered malware include:
- Lowering the bar of entry into more sophisticated malware attacks
- Reducing the creation timeline
- Including automated evasive behaviours making initial detection more difficult
- Using machine learning to blend in to its deployed environment to appear benign
Generative AI Phishing Campaigns
At the moment, there are usually some easy-to-spot identifiers when we see a phishing email come in to an email inbox. However ,generative AI will overcome many of the language barriers and formatting mistakes to make them much more difficult to identify.
Vishing threats (threats that mimic voice communications) will become more common too as the technology makes faking telephone conversations much easier.
Malicious phishing chatbots will also become more common.
Extended Detection and Response (XDR) to Mitigate 2024 Cyber Trends
In order to mitigate some of these AI-powered threats, you could deploy an open extended detection and response solution.
This provides sophisticated technologies backed up by a specialist SOC.
You fight AI with AI, using anomaly detection and machine learning algorithms, while employing automated remediation.
XDR is crucial to detect intrusion in real time, preventing threat actors from getting a foothold in your network.
Full Attack Lifecycle
A typical attack occurs across a number of stages, each of which can be detected by a XDR solution.
- Phishing via email
- Downloading the malware payload/lateral movement/elevating privileges
- Exfiltrating the data via FTP or PowerShell for example
- Encrypting systems and demanding ransom

2024 Cyber Trends Security Best Practice
Some of the ways to make sure your security posture is in the best condition it can be include:
- End user security awareness training (SAT)
- Inventory of all connected devices
- Maintain security patches for any and all operating systems
- Continuous monitoring across all major attack surfaces
- Understanding your business risk tolerance
- Have in place an incident response plan, processes and playbook
The New Normal: AI-Powered Novel Email Threats
In the second webinar from Barracuda, Richard Tubb and Nishant Taneja took at in-depth look at another 2024 cyber trend: how AI is playing a part in today’s email threats.
How SOCs were seeing more and more sophisticated ways AI was being used to enhance phishing attempts, and what technologies are being developed to better detect and isolate these threats.
Speakers:
The IT Business Growth Expert, Tubblog
and
Sr Director of Product Marketing, Barracuda Networks
How Are Cyber Criminals Leveraging AI to Bypass IT Security?
Email is still the primary risk surface for threat actors, and phishing the number one means of attack. Email is the doorway into our systems and data, and obtaining user credentials has become easier thanks to generative AI.
Cyber criminals are using Gen AI to generate targeted phishing campaigns, using social engineering to make attacks more specific to the individual targeted.
Gen AI has made phishing much easier to scale, and removed the language barrier for criminals targeting businesses all over the world.
2024 Cyber Trends: Top Ways Criminals Are Using AI
- Phishing (including QR code phishing)
- Malware Generation
- Deepfakes
- Content Localisation
- Access and Credential Theft
These AI generated attacks tend to come with better evasion too.
Whereas phishing emails have been easier to spot in the past, AI-powered phishing emails are much more difficult to discern.
Some of the tactics they’re employing include impersonating parties their victims have already had previous transactions with. This allows them to act like they’re continuing the conversation to catch them off-guard.
Generative AI can help attackers profile their victims before initiating their attack, giving them the opportunity to personalise their phishing attempts.
How Can We Detect and Protect Against These Novel AI-Powered Threats?
We need to deploy AI to fight AI, as basic gateway protection is no longer sufficient.
The earlier in the attack chain that AI can be used in detecting the threat, the better. If we can identify suspicious or anomalous behaviour before a breach occurs, the better our chances at preventing threat actors from stealing data, locking out systems and submitting a ransom.
The earlier in this chain that AI can help, the better:
- Step1: Account Credentials
- Step2: Network Compromise
- Step3: Lateral Movement
- Step4: Data Exfiltration
- Step5: Ransom Demand
What Steps are Barracuda Taking to Help MSPs to Detect AI Threats Earlier?
A lot of technologies out there are aimed at the enterprise level. They’re often not multi-tenanted, and so aren’t suitable for MSPs.
Barracuda have a lot of experience in the field of cybersecurity, and today attacks are much more complex – often touching multiple attack vectors.
Therefore, to help MSPs, they need to take a depth of field approach to cybersecurity and cover a wide range of disciplines for maximum efficacy.
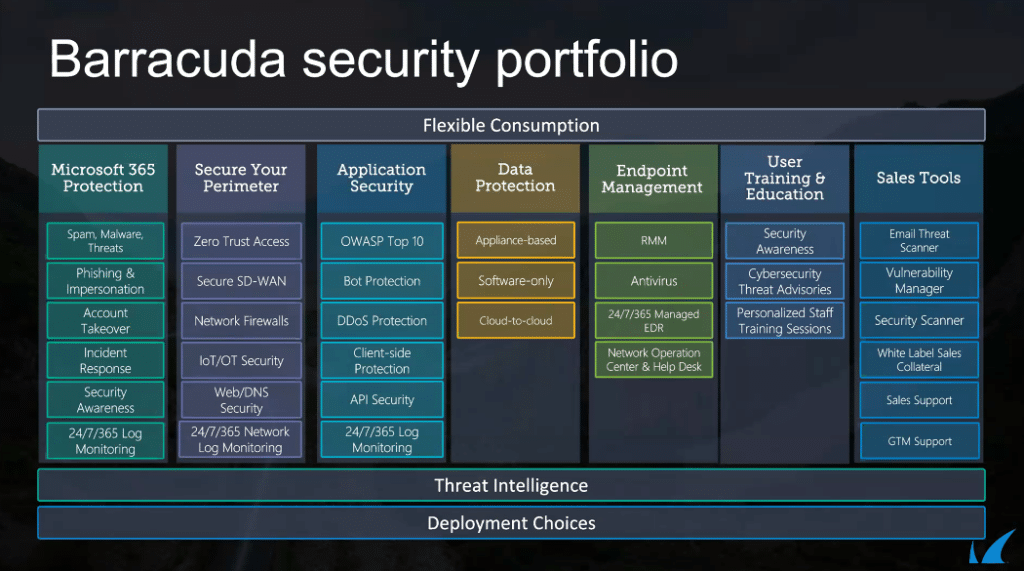
Barracuda’s security profile flexibly covers:
- Microsoft365 (spam protection, malware threats, phishing, account takeover, log monitoring, etc.)
- Secure Perimeter (zero trust, secure SD-WAN, firewalls, DNS security, IoT, etc.)
- Application Security (API security, DDoS and Bot protection, etc.)
- Data Protection – (application-based, software-only, cloud-to-cloud)
- Endpoint Management – (RMM, Antivirus, Managed EDR, etc.)
- User Training and Education (security awareness, threat advisories, personalised staff training)
- Sales Tools – (email threat scanner, vulnerability manager, white label sales collateral, etc.)
It all looks like a lot to manage for an MSP, which is why partnering up with a Security Operations Centre (SOC) gives you the extra resources and a quicker time to resolution when managing incidents and alerts.
Questions About AI-Powered Security
Q1: How Does AI Effectively Prevent Unauthorised Access?
AI can start getting to work, actively looking for suspicious behaviour, before a breach occurs. It can also take actions to quarantine, respond and remediate, given the workflows protocols that we set it.
Furthermore, the AI can identify areas to focus on for user training.
In partnership with the SOC, trends that you find affecting one of your client sites can fuel the intelligence across all of your sites.
Q2: How Can AI-Drive Email Security Reduce Alert Noise and Limit False Positives?
It’s a fine balance between being transparent and reducing the amount of traffic that comes the MSP’s way.
The idea is that by using machine learning, and fine tuning it through the SOC, the number of false positives should be reduced. Which, in turn, should reduce the alert fatigue for the MSP, while improving the efficacy of the product.
Q3: Privacy – How Can We Ensure AI and Machine Learning Technology Keeps Customer Data Private?
It’s important that the technology must be able to demonstrate that their AI uses aggregated data, and not have access to individuals emails, to protect their privacy.
The data modelling must be compliant with GDPR, or other regional regulations if you’re operating outside the UK.
Barracuda MSP Webinars on 2024 Cyber Trends
To watch both webinars on demand, please follow the registration links below:
Barracuda MSP Webinar: Top 2023 Cyberthreats to Watch for in 2024
Barracuda MSP Webinar: The New Normal: AI-Powered Novel Email Threats
Get the new eBook: Securing Tomorrow: A CISO’s Guide to the Role of AI in Cybersecurity
Spotlight on 2024 Cyber Trends Final Thoughts
2024 cyber trends put AI, especially generative AI, in the forefront for both threat actors and security professionals.
With the tools to increase the scale and sophistication of cyber attacks, coupled with more mature chains and greater attack surfaces, MSPs are looking more and more to externally managed security operations centres to protect their networks and the networks of their clients.
Barracuda MSP are constantly reviewing novel threats on the landscape, especially phishing, and are looking at using AI to intercept them.
Extended detection and response backed up by a dedicated SOC are recommended as part of your depth of defence strategy in 2024.
Are you concerned about AI-powered phishing attacks affecting your business? How are you preparing for the kind of threats we’re anticipating in 2024?
We’d love to hear about it in the comments.















Comments