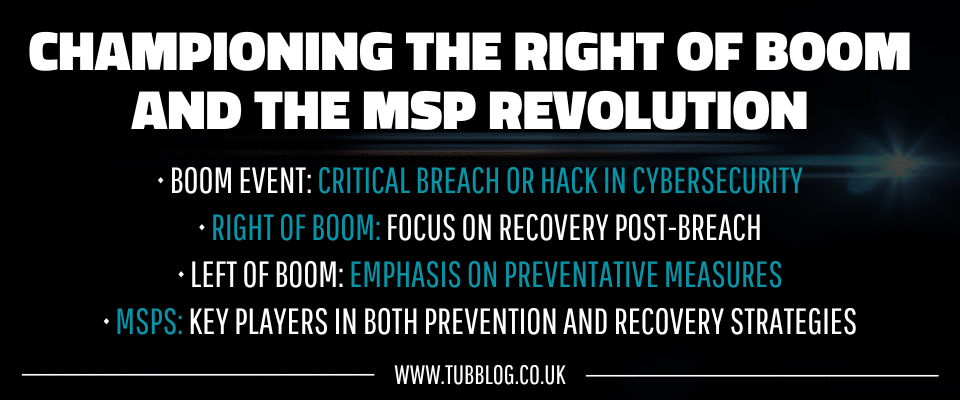
Cybersecurity experts often refer to a “Boom” event when discussing threats such as hacks or breaches. It’s a criticial event when there’s a network breach, database hack or device infection.
So, what do cybersecurity professionals mean when they talk about a “Right of Boom”?
It’s a phrase that’s fairly common in discussions regarding breach recovery and bouncing back from data loss. However, it’s rarely spoken of among MSPs.
In this guide, we’ll break down what the “Left” and “Right” of Boom mean and why it’s so important for even the smallest of IT companies to understand the difference.
What is a Cybersecurity “Boom?”
As mentioned briefly, a Boom is an inciting incident. It’s when a cybersecurity attacker successfully breaks through a company’s defences. We typically imagine Boom to sit in the middle of a breach sequence.
Therefore, we refer to “Left of Boom” as events that precede that midpoint and “Right of Boom” as events that follow it.
Put even simpler, Left is prevention, and Right is cure. For all you might focus more on the Right, both wings need equal attention.
What is “Left of Boom?”
Left of Boom refers to either the steps attackers take to breach data, or the preventative measures an MSP takes to secure client defences.
Left of Boom is where attackers start researching targets. It’s the reconnaissance stage – where they gather information, decide which attack types to use, and plan when to advance.
These plans don’t have to be meticulous. An attacker in the Left stage might use this period to design phishing emails or analyse the cybersecurity of a website.
For MSPs and cybersecurity experts, Left of Boom is all about prevention. The aim is to lessen or prevent Boom from happening, and if it does occur, to reduce the risk of sensitive data leaking.
That means taking the time to fortify network security, educate client staff, and prepare backups.
What is “Right of Boom?”
Right of Boom is where attackers inflict damage. It defines what an attacker does after they breach a company’s defences.
After Boom, an attacker might steal specific information – such as customer payment details and passwords – or take websites offline and hold critical data for ransom. Once you’re on the Right of Boom, it’s too late to stop a cybersecurity attack.
However, MSPs can strategise for Right of Boom by planning for data recovery and future backups and helping clients navigate compliance and public relations.
How can MSPs address Left and Right of Boom Cybersecurity Threats?
Now we’re clearer on what happens to the Left and Right of Boom, let’s look at some hypothetical strategies MSPs can use to protect their clients on either side.
Left of Boom
Here are some preventative measures MSPs and clients can take to reduce the risk of boom.
General Network Security
The best first defence against most attacks is a robust firewall. MSPs can use them to track suspicious traffic and block unauthorised attempts at accessing a network. Setting up a firewall is likely the first step you will take when arranging a Left of Boom cybersecurity strategy.
Updates and Patches
Updating all client software (no matter how innocuous) helps prevent attackers from abusing loopholes and vulnerabilities in older program versions.
MSPs should also take time to carefully patch programmes and services that might have previously flagged vulnerabilities. Time is of the essence to limit cybersecurity breaches!
Cybersecurity Education
Educating clients and users on the best security practices and principles can take many shapes and forms. Regardless, training people ensures companies protect data better in the event of a Boom and can add an extra human line of defence.
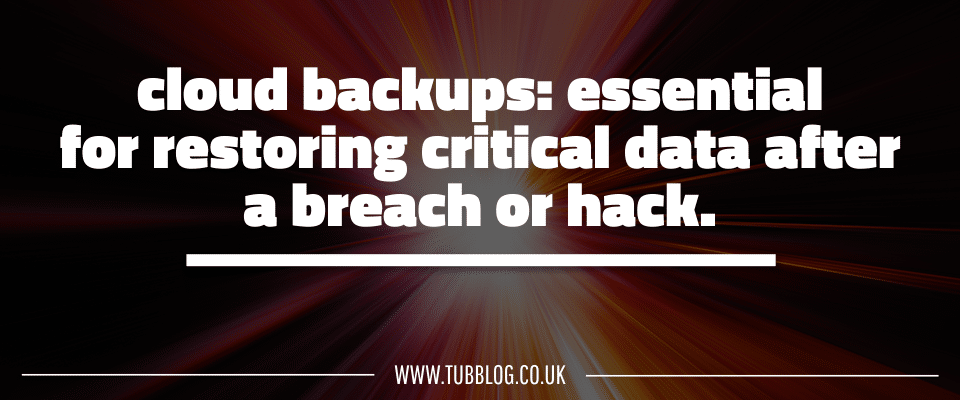
Data Backups
Regular data backups – ideally in the cloud – ensure companies can always restore critical information should they lose it in a cybersecurity breach or hack. The safest option in Left of Boom is to automate backups and keep hard copies on-site as an extra measure.
Network Segmentation
Segmenting a network, i.e. splitting it into smaller parts, can prevent wide-scale data loss. However, this option might not be suitable for all businesses and clients.
Access Control
Tightening controls through methods such as multi-factor authentication – where network users need to confirm access through multiple devices – can prevent sophisticated attacks. Educating users on healthy password strength and entropy is also good practice.
Auditing and Assessment
Regular auditing of security protocols and protections ensures that a client is always ready to fight against sophisticated attacks. An MSP must, therefore, be ready to regularly check software and security measures they have in place in line with evolving threats.
![]()
Right of Boom
At this stage, clients need to focus on recovering from boom – here are a few potential strategies.
Response Planning
Drawing up a response plan means ensuring a recovery process is efficient and effective. For example, a business should have a communications plan set up in the event of a data breach or attack, and clearly outline the steps they need to take if the worst scenario occurs. Testing mock responses is a healthy approach in Left of Boom.
Forensics
Analysing the nature of an attack helps businesses prepare for similar threats in future. MSPs should work to assess the extent of damage caused and where any potential vulnerabilities lie.
Disaster Recovery
Provided backup procedures are followed Left of Boom, MSPs can support clients by restoring cloud data to help them bounce back once a cybersecurity threat disappears. Disaster recovery plans are vital for businesses to return to normal.
Compliance and PR
All businesses should have compliance policies and procedures after a data breach. MSPs can help clients navigate policy and suggest how to communicate with affected parties.
Sources
- How to Organize Your Cybersecurity Strategy into Left and Right of Boom
- What Is Right & Left Of Boom With Cybersecurity?
- What Is Left & Right Of Boom?
- Organising Your Cybersecurity Strategy into Left and Right of Boom
- Defining Left of Boom and Right of Boom
- “Left and Right of Boom” – Having a Winning Strategy
- How to Organize Your Cybersecurity Strategy into Left and Right of Boom
- Cybersecurity Strategies: Left and Right of Boom – What does it Mean?
Conclusion
Regardless of whether or not you’ve heard of Left and Right of Boom, you must arrange your cybersecurity prevention and recovery strategies efficiently for all clients. Otherwise, they’re at risk of losing face with their own customers, and in turn, they’ll lose money.
Do you have any Left or Right of Boom strategies of your own? Feel free to share them in the comments below.















Comments